Cyber Security.
Made Simple.
Discover peace of mind with our three-tiered cyber security packages – SecureStart, SecureAware, and SecureComplete.
Partnering with the best to deliver industry leading cyber security services
Our Cyber Security services have everything you need to protect your business and empower your team
Secure your people
Your team is your first line of defence — and a common target. We help reduce human risk through practical training, phishing simulations, and clear security policies.
Working alongside trusted partners like the North East Cyber Crime Unit and IASME, we embed cyber awareness into your company culture, turning staff from potential vulnerabilities into confident defenders.
Popular Services
- Staff Education
- EMail Protection
- Human Risk Management
- Web content filtering

Protect your boundaries
Every device connected to your network is a potential entry point for attackers. We safeguard laptops, desktops, mobiles, and servers with advanced endpoint protection, proactive patching, and strict access controls.
By monitoring and managing device health, we ensure your technology remains secure, compliant, and ready for business.
Popular Services
- Endpoint Detection & Response (EDR)
- Mobile Device Management (MDM)
- Antivirus & Malware Protection
- Device Encryption

Expertly Deployed Secure Configurations
Misconfigurations are one of the leading causes of security breaches. We align your systems with recognised security frameworks, ensuring settings are hardened, permissions are correct, and unnecessary risks are removed.
From Microsoft 365 to on-premises servers, we keep your configurations optimised, compliant, and resilient against attack.
Popular Services
- Cyber Essentials Certifications
- Microsoft 365 Security Hardening
- Firewall & Network Configuration
- Multi-Factor Authentication (MFA) Enforcement

Keeping you informed
Cyber security is a journey. We provide continuous monitoring, incident response readiness, and regular security reviews to keep your defences strong.
With real-time alerts and proactive management, we stop threats before they become problems and keep you informed every step of the way.
Popular Services
- Security Operations Centre (SOC) Monitoring
- Vulnerability Scanning
- Incident Response Planning
- Client Portal with Reporting

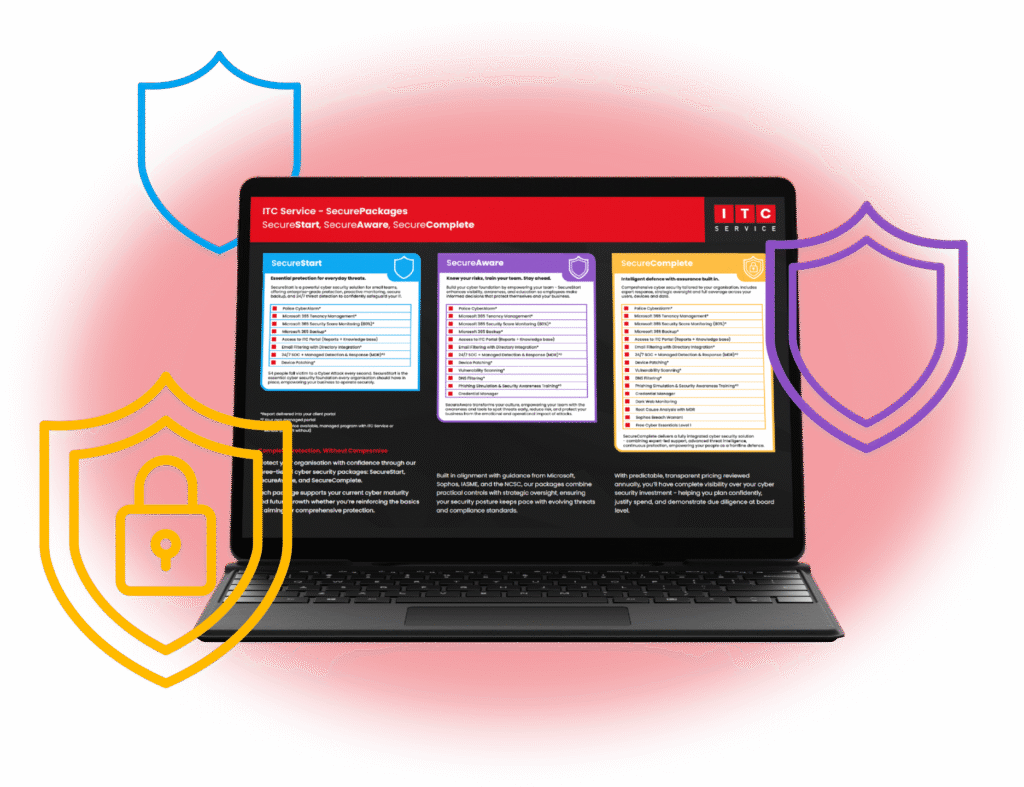
Our Cyber Security Packages
SecureStart
Essential protection for everyday threats.
Essential cyber protection including Microsoft 365 management, backup, email filtering, 24/7 SOC with MDR, device patching, and access to the ITC portal - built for scalable, best-practice security.
SecureAware
Enhanced security with proactive monitoring.
Adds vulnerability scanning, DNS filtering, and phishing simulations to SecureStart’s core protections - enhancing threat detection and user awareness for stronger, scalable protection.
SecureComplete
Fully managed, enterprise-grade protection.
Adds enterprise-grade tools for identity, insight, breach assurance, and dark web alerts — our most advanced protection, giving you complete coverage, compliance support and peace of mind.
Cyber Security: Investment vs. the Risk of Inaction Report
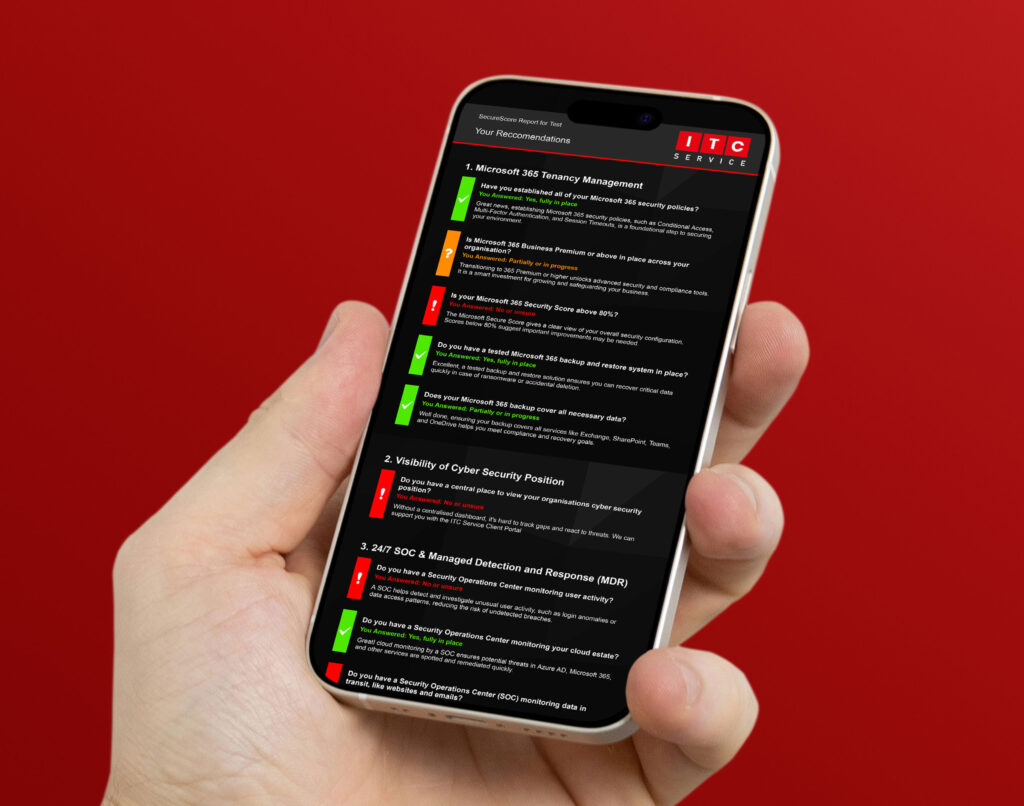
Discover Your ITC Service SecureScore
Our quick, multiple-choice assessment helps you measure your organisation’s cyber security readiness, informed by industry leaders including Microsoft, Sophos, IASME, and the NCSC.
You’ll receive a personalised Secure Score report, complete with clear, actionable recommendations to strengthen your defences and align with best practice.
It’s a simple way to gain valuable insight and take the next step towards a more secure, resilient IT estate.
Three Core Pillars of Cyber Security
Cyber security is a complex and ever-evolving field, and business owners or internal tech teams can’t be expected to handle it all. Since 2006, security has been at the heart of what we do.
Let ITC Service take care of your cyber security, so you can focus on driving your business forward.

Prevention
The first step in any robust cyber security strategy is protecting your digital boundaries.
This means deploying essential tools such as firewalls, Endpoint Protection, and Multi-Factor Authentication (MFA) to keep attackers out. Prevention is about staying ahead of potential threats by securing your systems, educating your users, and ensuring your defences are always up-to-date.
Detection and 24/7 Response
Even with strong prevention measures, threats can still slip through the cracks. That’s why continuous monitoring and threat detection are crucial.
Our advanced 24/7 Managed Detection and Response (MDR) team identify and respond to suspicious activities in real-time. Early detection of threats minimises damage, allowing you to act quickly and efficiently before a breach can escalate.
Business Continuity
When cyber incidents occur, the ability to recover and continue operating smoothly is essential. 60% of small businesses fail within six months of a data breach or a cyber attack.
Robust Business Continuity plans include regular backups, data recovery solutions, and disaster recovery strategies.
Your questions, answered.
Build True Resilience, Not Just Defence
What Is Security Scoring?
I use Multi-Factor Authentication, is that enough?
What are the biggest Cyber Security threats for SMBs right now?
The biggest cyber threats for SMBs in 2025 include ransomware, phishing, credential theft, and business email compromise – often targeting human error and unprotected systems.
Do you offer Cyber Security training?
Yes. From on-site educational courses demonstrating the importance of Governance, Risk & Compliance to Phishing awareness campaigns for internal teams, we’re prepared to train your team. We also collaborate with the North East Cyber Crime Unit to deliver security awareness training through in-person, interactive training sessions.
ITC Service Cyber Security Services

24/7 Managed Detection & Response
Fully managed 24/7 threat hunting, detection, and remediation, powered by Sophos, the world’s largest security operator.
This service provides proactive threat hunting, validation, and incident response from highly trained experts.
Email Filtering
Advanced email threat detection, using AI-powered technology to block malicious emails, including new and emerging threats.
Features include impersonation protection, email encryption, and data loss prevention.
Cyber Essentials Basic & Plus
Cyber Essentials showcases your business’s commitment to foundational Cyber Security controls.
As more businesses prioritise vendor compliance, Cyber Essentials is quickly becoming a necessity.
Human Risk Management
Identify user knowledge gaps and automate training to reduce risk. Through comprehensive phishing simulations and policy management.
Enterprise Credential Management
Our Enterprise password management solution uses a zero-trust, zero-knowledge architecture, offering far greater security than standard browser tools.
Get reports on breached passwords and action swift action.
Penetration Testing
There’s no better way to see if you’re secure than putting it to the test.
Our no-harm-done penetration testing services covers all aspects of a business. From detection to response and recovery.
Introducing our Cyber Security Packages
SecureStart, SecureAware, and SecureComplete offer scalable protection, tailored to your business.
From essential threat monitoring and Microsoft 365 management to advanced breach assurance and dark web alerts, each tier builds on the last – delivering expertly managed tools, proactive defence, and user-focused training.
Whether you’re just starting out or ready for enterprise-grade resilience, our packages provide clarity, confidence, and complete control over your cyber security posture
SecureStart
Essential protection for everyday threats.
Get started with the core tools to defend your business from common cyber risks—ideal for smaller teams and designed to protect the very basics of your IT estate.
- Police CyberAlarm*
- Microsoft 365 Tenancy Management*
- Microsoft 365 Security Score Monitoring (80%)*
- Microsoft 365 Backup*
- Access to ITC Portal (Reports + Knowledge)
- Email Filtering with Directory Intergration*
- 24/7 SOC + Managed Detection & Response (MDR)*2
- Device Patching*
Secure Start represents the bare minimum an organisation should have. 54 people fall victim to a cyber attack, every second. This package has the ability to stop the most common threats.
SecureAware
Enhanced security with proactive monitoring.
Go beyond the basics with advanced threat detection, real-time monitoring, and improved compliance. A solid choice for growing businesses that need peace of mind.
- Police CyberAlarm*
- Microsoft 365 Tenancy Management*
- Microsoft 365 Security Score Monitoring (80%)*
- Microsoft 365 Backup*
- Access to ITC Portal (Reports + Knowledge)
- Email Filtering with Directory Intergration*
- 24/7 SOC + Managed Detection & Response (MDR)*2
- Device Patching*
- Vulnerability Scanning*
- DNS FIltering*
- Phishing Simulation & Security Awareness Training*3
Secure Aware is for any business looking to operate at a Cyber Essentials level. It’s a great package for a growing business who need an industry standard level of protection
SecureComplete
Fully managed, enterprise-grade protection.
Comprehensive cyber security tailored to your organisation. Includes expert response, strategic oversight and full coverage across your users, devices and data.
- Police CyberAlarm*
- Microsoft 365 Tenancy Management*
- Microsoft 365 Security Score Monitoring (80%)*
- Microsoft 365 Backup*
- Access to ITC Portal (Reports + Knowledge)
- Email Filtering with Directory Intergration*
- 24/7 SOC + Managed Detection & Response (MDR)*2
- Device Patching*
- Vulnerability Scanning*
- DNS FIltering*
- Phishing Simulation & Security Awareness Training*3
- Credential Manager
- Root Cause Analysis with MDR
- Sophos Breach Warranty
- Dark Web Monitoring*
- Free Cyber Essentials Level One Certification
Get started with the core tools to defend your business from common cyber risks—ideal for smaller teams and designed to protect the very basics of your IT estate.





